SBU exposes Russian agent network
SBU cyber specialists exposed a large-scale agent network specializing in intelligence and subversive activities by the order of Russian special services.
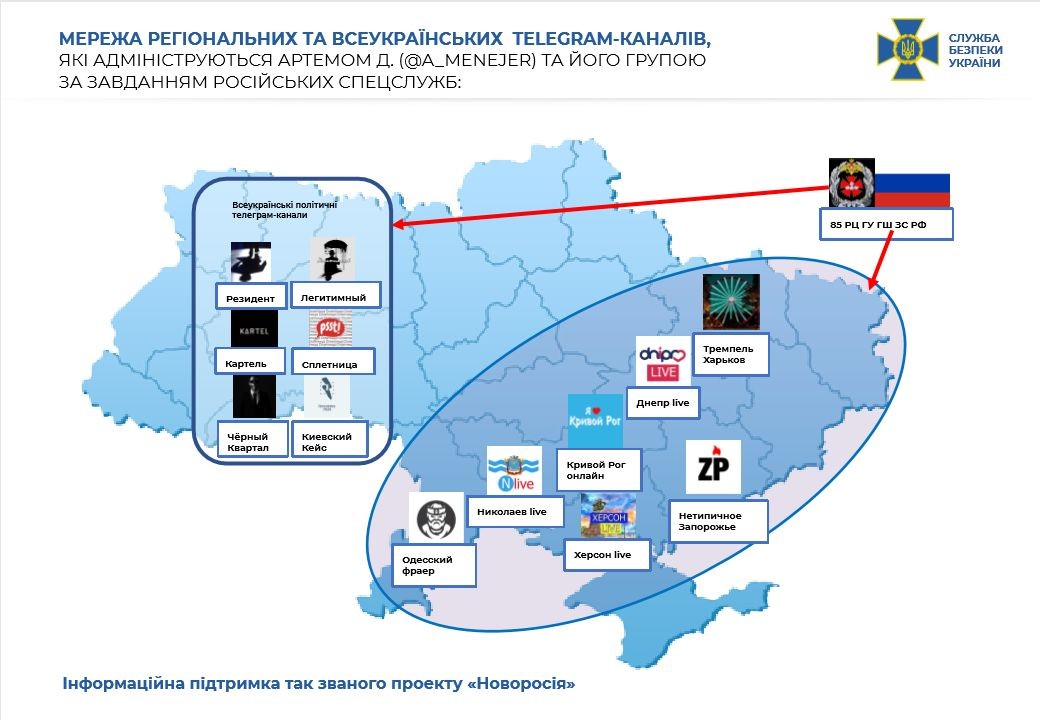
During a long-term operation, SBU operatives established that the intelligence network was set up by the so-called Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS), which included residents of Kharkiv and Odesa cities, as well as activists of the so-called Russian Spring.
They are currently operating from the Russia-controlled Pridnestrovian Moldavian Republic in Tyraspol city.
The Russian special services recruited Ukrainian citizens to create a number of political all-Ukrainian and regional Telegram channels, in particular, “Legitimnyi”, “Resident”, “Cartel”, “Spletnitsa”, “Chornyi kvartal”, “Politicheskii rasklad”, “Netypichnoe Zaporozzhye”, “Trempel Kharkov”, “Odessa fraer”, “Dnepr live”, “Nikolaev live”, "Kherson live".
Allegedly, the “chief manager” of the intelligence network was a resident of Odesa city. He organized pro-Russian disorders during the “Anti-Maidan” in the city of Odesa. Currently, the perpetrator is wanted under several articles of the Criminal Code of Ukraine.
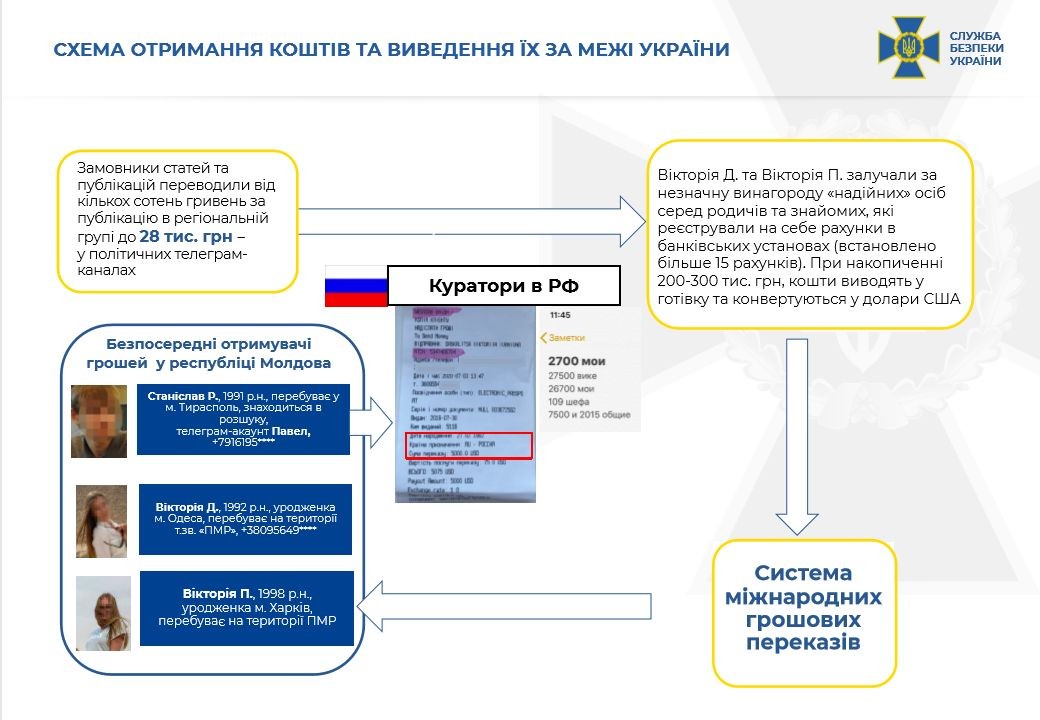
The offender personally managed 12 Telegram channels and communicated with the customers. Afterwards, he reported the work performed and agreed with Russian curators to publish illegal content on Telegram channel. The cost of the publications varied from several hundred hryvnias on regional channels and up to UAH 25-30,000 (USD 893-1072) on all-Ukrainian channels.
SBU officers has already identified 50 customers who transferred funds for the illegal publications. The suspects’ involvement in illicit activities against information security is being checked.
According to the linguistic and psychological conclusions, the agitprops disseminated information to create panic, aggravate and destabilize the socio-political and socio-economic situation in Ukraine via Telegram channels. Their core task was to discredit public authorities, influence public policy and artificially create internal pressure and incite citizens to protest.
The SBU also established that Russia's special services allowed network members to organize the monetization mechanism. The fraudsters obtained money via a network of accomplices who opened bank accounts in Ukraine. After that they converted money into currency and transferred to unrecognized Transnitria (TMR), Moldova or Russia.
As a result, law enforcement officers detained a Ukrainian citizen in city of Kyiv, one of the key suspect in the criminal proceedings. She and another member of the intelligence network were suspected of high treason.
Additionally, the operatives found alleged evidence of the detainee’s collecting classified information for the Russian intelligence services. SBU officers seized the electronic storage device with personal data of a large number of law enforcement officers. The detainee used it to commit illegal activities during the vacation in the Dominican Republic. The SBU has repeatedly received data on the use of the region about secret meetings between Russian agents and the intelligence network.
Further, the organizer of the network, hiding from the investigation abroad, was served a suspicion notice of high treason in absentia.
The operation was carried out by the SBU Office in Kharkiv region under the supervision of the Kharkiv Region Prosecutor's Office.